Recently-released attack code exploiting a critical Android vulnerability gives attackers a point-and-click interface for hacking a majority of smartphones and tablets that run the Google operating system, its creators said.
The attack was published last week as a module to the open-source Metasploit exploit framework used by security professionals and hackers alike. The code exploits a critical bug in Android’s WebView programming interface that was disclosed 14 months ago. The security hole typically gives attackers remote access to a phone’s camera and file system and in some cases also exposes other resources, such as geographic location data, SD card contents, and address books. Google patched the vulnerability in November with the release of Android 4.2, but according to the company’s figures, the fix is installed on well under half of the handsets it tracks.
“This vulnerability is kind of a huge deal,” Tod Beardsley, a researcher for Metasploit maintainer Rapid7, wrote in a recent blog post. “I’m hopeful that by publishing an E-Z-2-Use Metasploit module that exploits it, we can maybe push some vendors toward ensuring that single-click vulnerabilities like this don’t last for 93+ weeks in the wild. Don’t believe me that this thing is that old? Just take a look at the module’s references if you don’t believe me.”
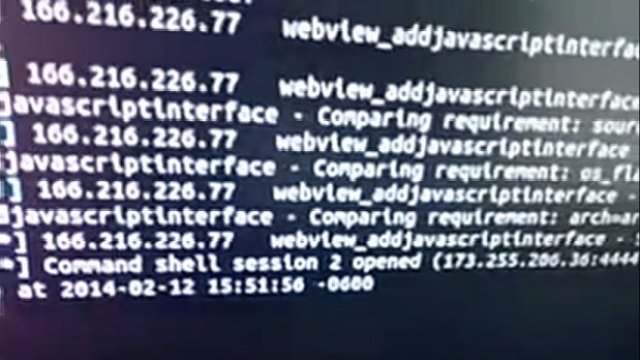
The WebView vulnerability allows attackers to inject malicious JavaScript into the Android browser and, in some cases, other apps. In turn, it helps attackers gain the same level of control as the targeted program. The easiest way to exploit the bug is to lure a vulnerable user to a booby-trapped webpage. Within seconds, the site operator will obtain a remote shell window that has access to the phone’s file system and camera. In some cases, the exploit can also be triggered by performing a man-in-the-middle attack while the victim is on an unsecured Wi-Fi network. By hijacking the app’s update process, attackers can gain control over the same resources already granted to the app, including permissions such as access to SD cards and geographic data.
Popping a shell
The threat is closely related to one Ars wrote about in September. In addition to making the native Android browser included in vulnerable versions of the mobile operating system susceptible, the weakness can also affect third-party apps developed with older code libraries. Readers can see a video of the newly released Metasploit exploit module in action here. The resulting command shell can do anything the native Android browser can do.
Rapid7’s Beardsley raises a good point about the proliferation of devices still running out-of-date versions of Android with known security vulnerabilities. Indeed, it’s not hard to find big-name sellers offering handsets that are vulnerable right out of the box. Ars has chronicled the checkered, slow history of Android updates before, as well as efforts by civil liberties groups to force US regulators to take action. Until carriers and sellers can be counted on to provide security updates for all their customers, the best bet for Android users is to use a Google-managed device such as the Nexus 4, which provides timely security updates directly from Google.
via E-Z-2-Use attack code exploits critical bug in majority of Android phones | Ars Technica.